前言
Cloudflare分析第一天:简单的算法反混淆
由上篇for (j = "10|8|5|9|1|4|0|2|3|6|7"["split"]('|')
可以看到循环的循序
case '6':o = (n = {},n["msg"] = f,n.cc = g,hF["VNwzz"](JSON["stringify"](n))["replace"]('+', "%2b"));continue;case '7':m["send"](i["TglBA"](i["iEKkH"]('v_', fy["_cf_chl_opt"]["cRay"]) + '=', o));continue;
提交之前先把数据转为字符串,再进行加密之后send
为了防止代码进入错误分支(第一天的分析中,只是为了定位加密的位置,调试出来的数据肯定是错误的),之后hook json来输出加密前的JSON数据
Hook代码:
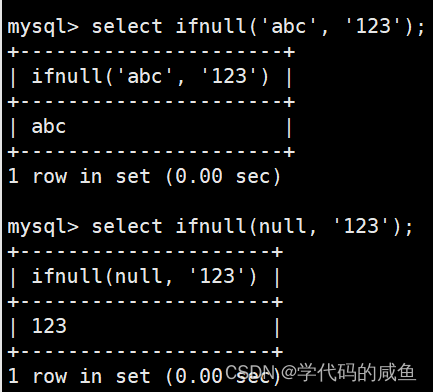
JSON_=JSON.stringify;
JSON.stringify=function(data) {console.log(JSON_(data));return JSON_(data);}输出如图:
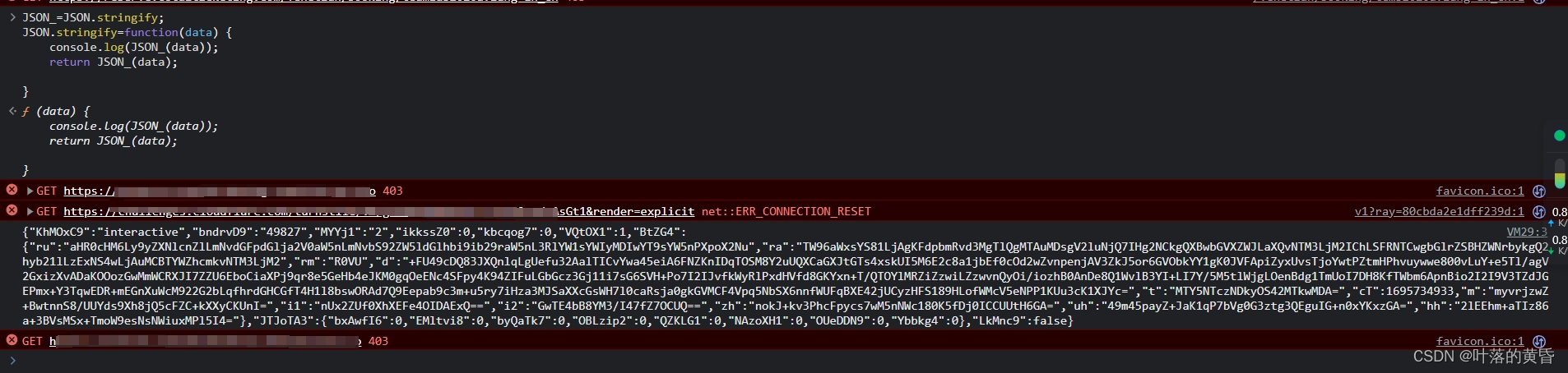
加密算法应该就是hF["VNwzz"]
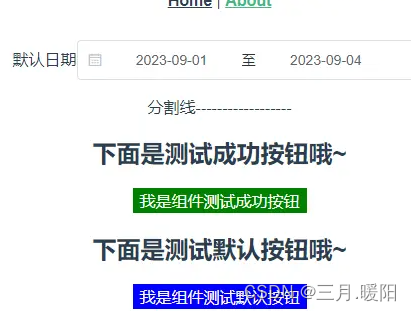
算法暂且不提,提交之后返还如图:
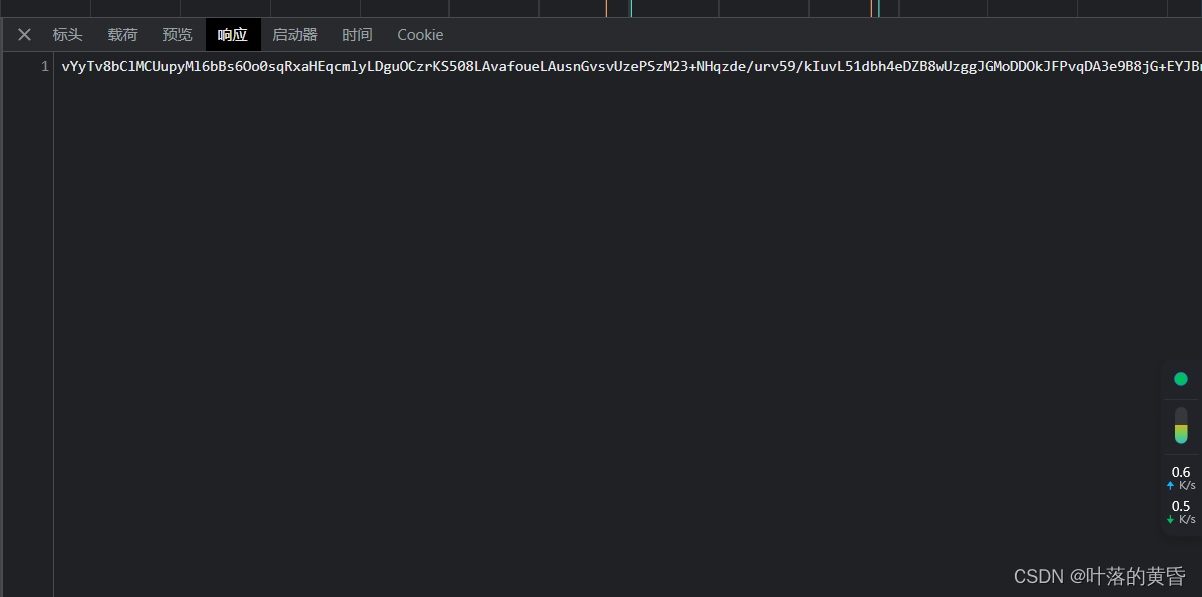
明显也是加密过的,既然返回,既然有后续,那么可以断定肯定可以解密的,找一下解密函数的位置.
从send往下跟(下面JS代码非第一篇中的JS代码了,是实时调试的代码,因为每次刷新JS内容都不一样,所以你们显示的代码跟我贴出来的不会相同,但是会类似)
i[jj(473)] = function(jm, l, m, n, o, s, u, v, w) {if (jm = jj,l = {},l["VWkdu"] = "unspun",m = l,n = "600010",i["readyState"] != 4)return;(o = this["getResponseHeader"]("content-type"),f["MMxvO"](o, f["SFsFE"])) && (s = JSON["parse"](i["responseText"]),s["err"] && (n = s["err"]));if (u = f["fzhiJ"](hj, n),u && f["fzhiJ"](hk, u),i["status"] === 400) {if ("QwWqw" === "QwWqw")return void fy["fUJhKx5"]();elsee(f, function(B, jn) {jn = jm,B[jn(274)][jn(448)] = jn(502),B[jn(274)][jn(1191)] = jn(496)})}if (f["mycqq"](i["status"], 200) && f["mycqq"](i["status"], 304)) {if (f["ZYzcT"]("Vjfpl", "Vjfpl"))return void f["AQGEw"](h);elsee("spinner-icon", function(C, jo) {jo = jm,C[jo(1878)][jo(397)](m[jo(1372)])}),f(f["YBWCH"])}(v = gc(i["responseText"]),v["startsWith"]("window._")) ? new fy[("Function")](v)(d) : (w = g2(v),f["jKZSc"](typeof w, "function") && w(d))
}
可以看到得到i["responseText"],会经过函数gc,然后根据gc内容进入两个分支,应该是不同版本的Cloudflare的原因,也可以是跟请求次数的原因,这个留着后面再看!
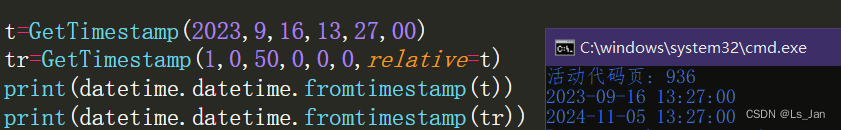
这里返回的V内容如图:
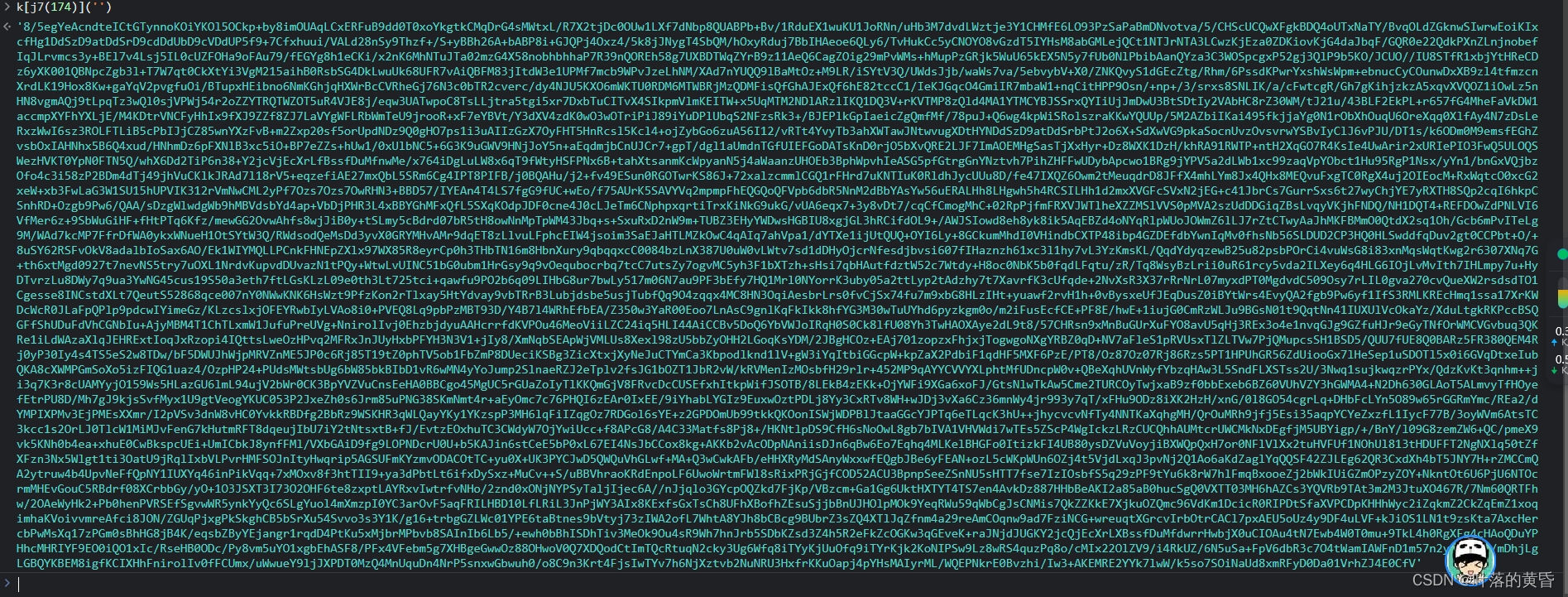
明显跟分支一的判断条件v["startsWith"]("window._"))不相关,那就是走第二个分支(w = g2(v),
f["jKZSc"](typeof w, "function") && w(d))
先把v经过函数g2复制给w,判断w是不是一个function,是的话用运行函数w 传入的参数是d,
记录一下d的值是:
{"KhMOxC9":"interactive","bndrvD9":"6653","MYYj1":"2","ikkssZ0":0,"kbcqog7":0,"VQtOX1":1,"BtZG4":{"ru":"aHR0cHM6Ly9yZXNlcnZlLmNvdGFpdGlja2V0aW5nLmNvbS92ZW5ldGlhbi9ib29raW5nL3RlYW1sYWIyMDIwYT9sYW5nPXpoX2Nu","ra":"TW96aWxsYS81LjAgKFdpbmRvd3MgTlQgMTAuMDsgV2luNjQ7IHg2NCkgQXBwbGVXZWJLaXQvNTM3LjM2IChLSFRNTCwgbGlrZSBHZWNrbykgQ2hyb21lLzExNS4wLjAuMCBTYWZhcmkvNTM3LjM2","rm":"R0VU","d":"GLaiWK7+Aynp53e83DlICIPs5kPXyow7ZJCuyNtNUjK0jVYAnt+TbytmxWrcP+62RSFFXIPuPmb/3fbHixQTprOyAwChBbvM1MrAvfjlmXW6qkuXmRFOKuykwiPuP3DMHmmaC63qr/9BJ+yhj2PzrjTA952Vb9Su06wVTdu7kEqdvr8OieyHZCkOpa+lGKgP/c6gQgEFq6S8VyKgGecCBuxJ56f14LFIYU2oNONruHPciGevRsu5QOgcMsbuwvMHB9JeIQK59eMH9M4J7rru11sjzPYBJLctT93PUSVKYS4dmYcFsb0dj/6RX7y3ODNkmURLa3vso3UJByrBLVZ5IuVymXA87PlT+VLbdfBMyJbXP7xStKwqEmxlbnp9VLzvtAnTkVFY8DSIuvnUSjqQWnNnQvAr3RPIDxrQbSNgVzdV+g3bHulxk6UCVIV1PN7SMvsZ+NAFFzVvhBjXOJEKEOpgEvhjL+0KYUSx9h0/yQBzAsPL/0GC8O7wwAyttYwfGhRNud5X+76dmcm9xKMV92iQrREz3f/6EMIgpNbnhzs=","t":"MTY5NTczNTI1My4zNDQwMDA=","cT":1695735254,"m":"2nCYUb/c8IGLtnA7v0cShWvIPXJfl/OTJmP5UNxF+1w=","i1":"X+hEwD3IazR/zARQ0f6Vsg==","i2":"2zPnYa8F0C5i9HwWO/A93A==","zh":"nokJ+kv3PhcFpycs7wM5nNWc180K5fDj0ICCUUtH6GA=","uh":"49m45payZ+JaK1qP7bVg0G3ztg3QEguIG+n0xYKxzGA=","hh":"2lEEhm+aTIz86a+3BVsMSx+TmoW9esNsNWiuxMPl5I4="},"JTJoTA3":{"bxAwfI6":0,"EMltvi8":0,"byQaTk7":0,"OBLzip2":0,"QZKLG1":0,"NAzoXH1":0,"OUeDDN9":0,"Ybbkg4":0},"LkMnc9":false}
貌似跟刚hook JSON输出的内容一样.
w的函数内容是:
function fI(i, j, l, n, o, s, u, v, w, ig, x, B, C, D) {return ig = ia,x = {},x["VLuHS"] = "QTvFm",x["UFwjI"] = function(E, F) {return F * E},x["eQQaR"] = function(E, F) {return E < F},x["DMIyJ"] = function(E, F) {return E ^ F},x["kBIZP"] = function(E, F) {return E ^ F},x["hRCDz"] = function(E, F) {return F ^ E},x["uPoTE"] = function(E, F) {return F ^ E},x["CGyfQ"] = function(E, F) {return E ^ F},x["bKlIO"] = function(E, F) {return E ^ F},x["ckUij"] = function(E, F) {return E ^ F},x["EfMnC"] = function(E, F) {return F ^ E},B = x,C = this,D = this.h[133 ^ this.g],this.h[B["uPoTE"](9, this.g)]["push"]([NaN, '', '', 0], this.h[B["bKlIO"](97, this.g)]["length"], 20),this.h[B["uPoTE"](68, this.g)] = j,this.h[this.g ^ 139] = l,this.h[this.g ^ 149.42] = n,this.h[126 ^ this.g] = o,this.h[72 ^ this.g] = s,this.h[254.22 ^ this.g] = u,this.h[this.g ^ 26] = v,this.h[135 ^ this.g] = w,this.h[this.g ^ 133.86] = i["slice"](),function(ih, E, F) {for (ih = ig,E = {'YBIKS': ih(1687),'HjGch': B[ih(167)],'BmmCx': function(G, H, ii) {return ii = ih,B["UFwjI"](G, H)},'Tkrye': ih(1527),'SSwvN': function(G, H, ij) {return ij = ih,B[ij(1303)](G, H)}},F = {}; !isNaN(C.h[B[ih(376)](133, C.g)][0]); F = {'j': F.j},F.j = C.h[B[ih(1187)](133, C.g)][3] ^ 87 + C.h[B[ih(1861)](133, C.g)][1][ih(433)](C.h[B[ih(954)](133, C.g)][0]++) & 255.69,function(G, ik, H) {return ik = ih,H = {'Ljnku': E["YBIKS"],'AjvvY': E["HjGch"],'IPsXd': function(I, J) {return I + J},'BkFWt': function(I, J, il) {return il = ik,E[il(194)](I, J)},'zbNLn': function(I, J) {return J !== I},'gBDEx': E["Tkrye"],'aYteo': function(I, J) {return I ^ J},'GRFey': function(I, J, im) {return im = ik,E[im(1664)](I, J)},'LoecI': function(I, J) {return I ^ J}},function(io, I, J, N, K) {if (io = ik,I = {'ApVtT': H["Ljnku"],'ALfoN': function(L, M) {return L(M)},'BbJsM': function(L, M, N, O) {return L(M, N, O)}},"UbZvD" === H["AjvvY"])return !s(I["ApVtT"]) && I["ALfoN"](C, "cookies_missing"),![];else {J = (J = C.h[133.64 ^ C.g],J[3] = H["IPsXd"](H["BkFWt"](28083, J[3] + G.j), 13090) & 255,C.h[G.j ^ C.g]);try {H["zbNLn"]("tCuMr", H["gBDEx"]) ? (G = "symbol" !== typeof o ? s + '' : u,N = {},N["enumerable"] = !0,N["configurable"] = !0,N["writable"] = !0,N["value"] = void 0,v in w ? I["BbJsM"](x, B, C, N) : D[E] = void 0) : J["bind"](C)(G.j)} catch (N) {if (J = C.h[H["aYteo"](97, C.g)],H["GRFey"](0, J["length"]))C.h[H["aYteo"](155, C.g)] = N,K = J["pop"](),C.h[133 ^ C.g] = J["pop"](),C.h[H["LoecI"](9, C.g)]["splice"](K);elsethrow N}}}}(F)());return C.h[B[ih(1446)](135, C.g)]}(),this.h[B["ckUij"](133, this.g)] = D,this.h[B["EfMnC"](20, this.g)]
}
给自己留个备注: 暂时没看到解密出来的明文数据,需要进一步分析
![[C++ 网络协议] 异步通知I/O模型](https://img-blog.csdnimg.cn/6107f8eecc204eedb99d161d0d3d838e.png)